Public clients like Native mobile applications or Single Page Applications cannot securely store Client Secret in Authorization Code grant type. Decode source of the mobile application or view source code of Single Page Application, we can see this Client Secret information. So OAuth introduces Proof Key for Code Exchange (PKCE) extension support for Authorization Code grant type to solve this problem. How is it in detail? In this tutorial, we will learn about the Authorization Code grant type with Proof Key for Code Exchange (PKCE) in OAuth 2.1!
The idea of PKCE is to use a pair of secret codes including Code Challenge and Code Verifier, generated by a third-party application called Client Application. The Client Application will send a Code Challenge along with the request to get the authorization code. The authorization server will save this Code Challenge. In request to get the access token, the Client Application will send Code Verifier, the authorization server will verify Code Challenge and Code Verifier to issue access token.
Workflow of Authorization Code grant type with PKCE, I can express as follows:
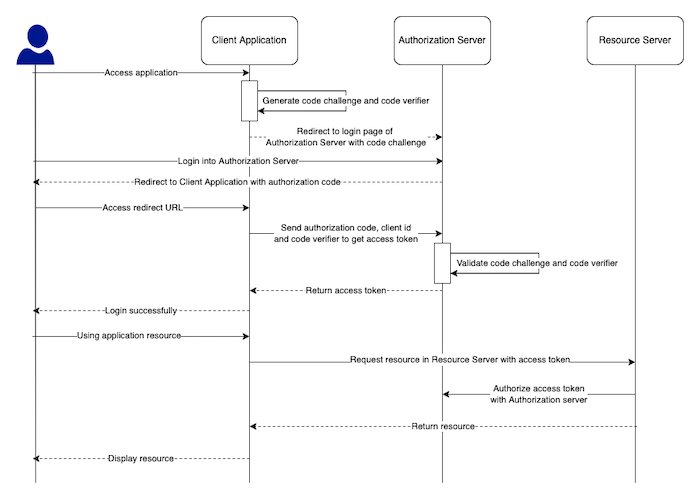
As you can see, Client Secret is no longer used in the grant type of Authorization Code with PKCE!



