OAuth (Open Authorization) 2.0 is a standard that defines how third-party applications can access user information and resources related to this user in another application. It makes it possible for third-party applications to access resources without knowing the credentials of the user who owns those resources, by using an access token. It solves a number of problems and limitations traditionally encountered by third-party applications that want to use resources owned by a particular user:
- Third-party applications must store user credentials including username and password to use for authentication.
- The server providing the user’s resources must support password authentication for authentication from third-party applications.
- Third-party applications can access resources without any restrictions, we cannot restrict them to only access certain resources, nor can we restrict how long they can access resources, …
- Users who own resources cannot revoke access for some third-party applications, must revoke access for all of these applications, by changing the password for example.
- …
OAuth 2.0 solves these problems by introducing an authorization layer that separates the roles of third-party applications from user’s resources. In OAuth 2.0, third-party applications request resources that are managed by the user and provided by the resource server. They must use the access token, define which resources they can access, how long, etc., to request resources. How is the specification? In this tutorial, I will give you an overview of OAuth 2.0!
The first thing you need to know is about the OAuth 2.0 Role.
In short, Roles in OAuth 2.0 are components that will participate in the process of authenticating user information and resources that third-party applications need to use. These Roles include:
- The resource owner is an entity that has permission to grant access for third-party applications to resources. If the resource owner is human, the resource owner is the end-user who owns these resources.
- A resource server is a server that contains resources that third-party applications need to access. It will rely on the access token that the third application is requesting to the resource to determine if this application has access to the resource or not?
- The third applications or we often call them Client Applications, are the applications that will use the access token to request resources provided by the resource server.
- The authorization server is the server that will issue the access token after successfully authenticating the resource owner.
You can see the following figure for more understanding.

In the figure above, the Resource Owner is the end-user who owns the resources. The Client Application can also use the Client ID information to represent itself to request resources.
Usually, you will see Resource Server and Authorization Server will be one, for example, we just need to use Google for Resource Server and Authorization Server. But of course, we can separate them as well.
To visualize the process of authenticating user information in OAuth 2.0, please see the following figure:
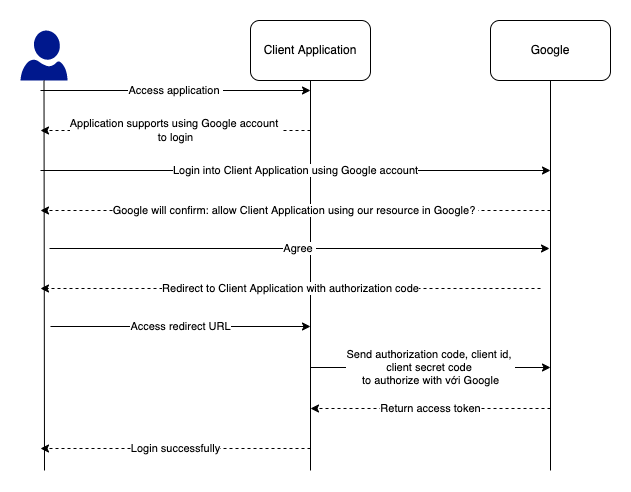
The figure above illustrates the case where the Client Application requests a user’s resource provided by Google.
We will access the application we want to use. To be able to use Google’s resources, the Client Application will redirect to Google’s login page for us to log in.
After successfully logging in to Google, Google will ask if you allow this application to access our resources or not? If you agree, Google will redirect to the Client Application with the URL previously registered by this application with Google, along with the authorization code.
At that time, the Client Application will use the provided information including authorization code, client id, and a client secret to confirm with Google to access our information at Google.
Google will then return an access token that allows the Client Application to access our information.
At this point, the Client Application can use the resource with the access token without any more authentication.
Above is the basic information, an overview of OAuth 2.0, I will guide you on how to implement OAuth 2.0 for your application in the incoming tutorials.




Hung
Cảm ơn tác giả!