The JSON Web Key Set is a collection of JSON Web Key public keys provided by the Authorization Server so that the Resource Server can verify the access token sent by the Client Application. In the tutorial about implementing OAuth Authorization Server using Spring Authorization Server, I showed you how to define this JSON Web Key using code. But for applications running in production, for security reasons, the JSON Web Key information will often be managed by another party, possibly the IT team. They will generate a keystore file, our task is to use this keystore file to define the JSON Web Key Set. In this tutorial, I will show you how to define JSON Web Key Set for Authorization Server using Spring Authorization Server and PKCS12 key store file.
First, I will generate a keystore file with PKCS12 format as an example.
The following results:
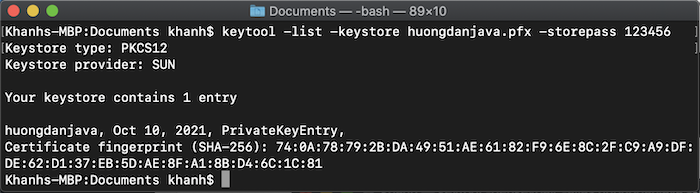
Usually, we will expose the environment variable pointing to the path of the .pfx file for their IT team to configure. But for the sake of simplicity in this tutorial, I will put this .pfx file in the src/main/resources folder of the example project in the tutorial Implement OAuth Authorization Server using Spring Authorization Server:
We will initialize Java Security’s KeyStore object to hold the information of the .pfx file as follows:
|
1 |
KeyStore keyStore = KeyStore.getInstance("pkcs12"); |
There are several overloads of the getInstance() method that you can use. Here, I am using getInstance() with the parameter being the type of the keystore file. You can see all the keystore types that Java supports here.
If you use a password to protect the keystore file, you can get the content of the keystore file as follows:
|
1 2 3 |
try (FileInputStream fis = new FileInputStream("src/main/resources/huongdanjava.pfx")) { keyStore.load(fis, "123456".toCharArray()); } |
123456 is the password of keystore file.
After you have loaded the content of the keystore file, you can convert this content to the JWKSet object of the Nimbus library, the library that Spring Authorization Server is using to work with the access token, as follows:
|
1 2 3 4 5 6 |
JWKSet jwkSet = JWKSet.load(keyStore, new PasswordLookup() { @Override public char[] lookupPassword(String name) { return "123456".toCharArray(); } }); |
When converting the content of the keystore file to the JWKSet object, we need to pass the password information of the private key. With keystore type PKCS12, the password of the private key is the same as the password of the keystore file.
The entire content of the method to build my JWKSet object information is as follows:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 |
private JWKSet buildJWKSet() throws KeyStoreException, NoSuchAlgorithmException, CertificateException, FileNotFoundException, IOException { KeyStore keyStore = KeyStore.getInstance("pkcs12"); try (FileInputStream fis = new FileInputStream("src/main/resources/huongdanjava.pfx")) { keyStore.load(fis, "123456".toCharArray()); return JWKSet.load(keyStore, new PasswordLookup() { @Override public char[] lookupPassword(String name) { return "123456".toCharArray(); } }); } } |
You can use this method when building your Authorization Server using Spring Authorization Server! Declare the JWKSource object now in the Spring container as follows:
|
1 2 3 4 5 6 7 |
@Bean public JWKSource<SecurityContext> jwkSource() throws NoSuchAlgorithmException, KeyStoreException, CertificateException, FileNotFoundException, IOException { JWKSet jwkSet = buildJWKSet(); return (jwkSelector, securityContext) -> jwkSelector.select(jwkSet); } |
You can use the JWKSet build code for any keystore!



Robert ll.
Hello, I am new to spring security, I would like to know,
What is the purpose of using these certificates PKCS12 ?
Will it be necessary to distribute the certificate for each client that wants to access the rest api?
Robert ll.
Hello, I am new to spring security, I would like to know,
What is the purpose of using these certificates?
Will it be necessary to distribute the certificate for each client that wants to access the rest api?
Abbas MG
Hi Khanh
I use PKCS12 key without any problem. but my resource server not working.
what do i for spring resource server?
sorry for my english skill problems 🙂
Khanh Nguyen
What was your problem @Abbas?
Abbas MG
my spring resource-server can not connect to authorization-server when change key to PKCS12 in authorization-server
Khanh Nguyen
Did you take a look on this tutorial https://huongdanjava.com/implement-oauth-resource-server-using-spring-security-oauth2-resource-server.html @Abbas?
Abbas MG
no 😐
I will read this tutorial, thank you 🙂
Niall
Hi Khanh,
Thank you for putting this article together. I am attempting to substitute my own .pfx file into the code from your tutorial on creating a Spring Authorization Server. I did follow along your VERY helpful post on Generating keystore using keytool in Java. However, now, when I run my code (your code from git actually!), but substitute in my new pfx file, it cannot run as a java.io.IOException is thrown with the following output: “DER input, Integer tag error”
I was wondering if you experienced this and if you have any pointers. By the way, do you have a ko-fi account or similar where I could send you a few Euro to thank you for your help so far?
Khanh Nguyen
Hi Niall,
Did you already take a look this https://stackoverflow.com/questions/59934676/keytool-error-java-io-ioexception-der-input-integer-tag-error?
I didn’t encounter this error yet. If possible, can you give me what you did to generate the .pfx file? I can try in my side.
I have Paypal account paypal.me/khanhnguyenj and also Ko-fi account Ko-fi.com/khanhnguyenj @Niall. Thanks you.
Niall
Hey Khanh,
Thank you for the link. BUt I am not sure it helps me. What I did was a two step process:
To generate my own pfx file I ran:
1. keytool -genkeypair -alias auth-server -keyalg RSA -keystore “C:/Program Files/Java/jdk1.8.0_291/jre/lib/security/cacerts” -keypass password123 -storepass changeit -storetype PKCS12
Then, to export this as a pfx file (so I could import it into src/main/resources of the project) I ran:
2. keytool -exportcert -keystore cacerts -alias auth-server -file auth-server.pfx
(just sent you a thank you on PayPal!)
Khanh Nguyen
Hi Niall,
To get the .pfx file, you only need run one command, for example:
and then put the generated .pfx file into the src/main/resources folder.
Can you try again?
P/S: I received your donation, thank so much.
Sandeep YANDRA
When you point output path to program files .. you are supposed to open command prompt as administrator ..
Point out to any other folder which you have access like downloads/documents/d drive/ etc .