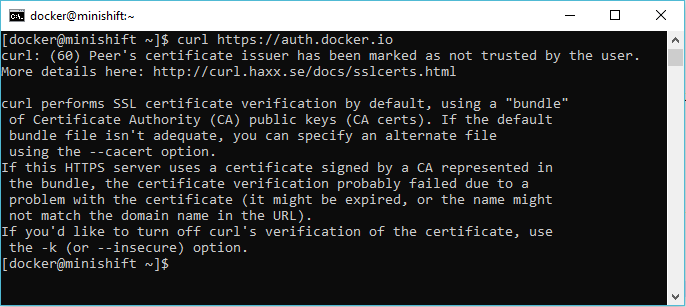
When working with networks that require security, if we request to sites that use HTTPS, we will often encounter issues related to the SSL certificate, my example is as follows:
|
1 2 3 4 5 6 7 |
[docker@minishift ~]$ curl https://auth.docker.io curl: (60) Peer's certificate issuer has been marked as not trusted by the user. More details here: http://curl.haxx.se/docs/sslcerts.html curl performs SSL certificate verification by default, using a "bundle" of Certificate Authority (CA) public keys (CA certs). If the default bundle file isn't adequate, you can specify an alternate file using the --cacert option. If this HTTPS server uses a certificate signed by a CA represented in the bundle, the certificate verification probably failed due to a problem with the certificate (it might be expired, or the name might not match the domain name in the URL). If you'd like to turn off curl's verification of the certificate, use the -k (or --insecure) option. |
To resolve this error, we need to download the certificate for that site and save it to the Trusted Certificate Authority of the operating system.
To do this, the first thing we will use is an OpenSSL command to save the certificate of the site, the syntax of this command is as follows:
|
1 |
openssl s_client -showcerts -connect {HOST_NAME}:443 -servername {HOST_NAME} </dev/null | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > {FILE_NAME}.pem |
Therein, HOST_NAME is the name of the website you are having problems with, FILE_NAME is the name of the file after we save the certificate.
In my case, I will run the following command:
|
1 |
openssl s_client -showcerts -connect auth.docker.io:443 -servername auth.docker.io </dev/null | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > auth.docker.io.pem |
Once the certificate has been saved, copy the file to /etc/pki/ca-trust/source/anchors/ of CentOS and run the following command to update the Trusted Certificate Authority:
|
1 |
sudo update-ca-trust extract |
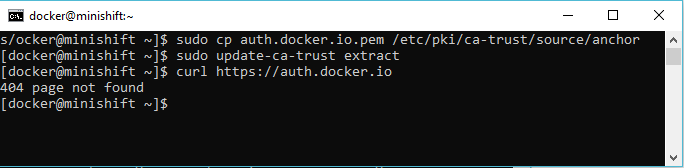
Mine is as follows:
|
1 2 3 |
sudo cp auth.docker.io.pem /etc/pki/ca-trust/source/anchors/ sudo update-ca-trust extract |
Results after updating the certificate: